Cryptocurrencies have exceedingly grown in popularity among investors, customers, developers, and regulators. However, a significant barrier to novice participants are the various terms floating around the industry. Many terms come from computer programming while other more recent terms originate from slang words or phrases. This post will go through some of the most common cryptocurrency terms, offering a solid basis for interested individuals.
#A
ATH
“ATH” is an abbreviation for “All-Time High.” It is the highest price point that a cryptocurrency has been in its trading history.
ATL
“ATL” is an abbreviation for “All-Time Low.” It is the lowest price point that a cryptocurrency has been in its trading history.
Address
An address is a destination where a user sends and receives digital currency. Addresses are usually composed of a long series of letters and numbers. Without an address, the blockchain can’t confirm nor verify the existence of a coin, so, without a wallet address, you can’t own a cryptocurrency.
Altcoins
Altcoins, or Alternative Coins, refer to cryptocurrencies other than Bitcoin.
Airdrop
An airdrop is a distribution of a cryptocurrency token, usually for free, to numerous wallet addresses. Airdrops are primarily implemented as a marketing campaign as a way of gaining attention and new followers.
Arbitrage
Arbitrage is the practice of simultaneously buying and selling the same asset in different markets to take advantage of price differences between the markets.
Ashdraked
Ashdraked is a term born from Crypto trading and conveys a situation of complete loss of a trader’s total invested capital.
Atomic Swap
An atomic swap is a smart contract technology that enables the exchange of one cryptocurrency for another without using centralized intermediaries, such as exchanges.
AMM
An automated market maker (AMM) is a type of decentralized exchange protocol that relies on a mathematical formula to price assets. Instead of using an order book like a traditional exchange, assets are priced according to a pricing algorithm.
#B
Blockchain
The technology that underpins cryptocurrency is known as a blockchain. It is a distributed and immutable digital ledger composed of all the transactions ever made in a cryptocurrency. The name comes from its structure, in which individual records, called blocks, are linked together in single list, called a chain.
Bull
If a trader believes that an asset will rise in value, he or she is a “bull.” When an investor has this optimistic expectation of an asset’s future, the frame of mind is described as “bullish.”
Bear
Someone who believes that prices in each market will decline in future is a “bear”. Bearish traders might take a short position on an asset that will pay off should the asset in question fall in value.
Byzantine Generals’ Problem
The Byzantine Generals Problem describes a situation where communication that requires consensus on a single strategy from all members within a group or party cannot be trusted or verified. It is used to describe the difficulty decentralized systems have in agreeing on a single truth. The Byzantine Generals Problem plagued money for millennia, until the invention of Bitcoin which uses a Proof-of-Work consensus mechanism and a blockchain to solve the Problem.
Block
A file containing information on transactions completed during a given time period. Blocks are the constituent parts of a blockchain.
Block Explorer
A block explorer is a blockchain search engine that enables a user to view details of blocks on a given blockchain.
Block Height
A value describing the number of blocks preceding a given block in the blockchain.
Block Reward
The coins awarded to a miner or group of miners for solving the cryptographic problem required to create a new block on a given blockchain.
Block Size
Block size refers to the amount of data about transactions a single block in the chain can carry.
Block Time
Block time refers to the approximate time it takes for a blockchain-based system to produce a new block.
Bid-Ask Spread
Bid-ask spread is the difference between the highest price which a buyer is willing to pay for an asset as well as the lowest price that a seller is willing to accept.
Bagholder
An investor who continues to hold large amounts of a specific coin or token, regardless of its performance.
A chart pattern where price witnesses a sudden spike in one direction, followed by consolidation and a sudden spike to the opposite direction ending close to the base price. The pattern resembles the shape of the head of the iconic Simpsons character, Bart Simpson.
BIP
Bitcoin Improvement Proposal (BIP) is the standard format for documents proposing changes to the Bitcoin protocol.
BEP-20 is a Binance Smart Chain token standard, that extends ERC-20, the most common Ethereum token standard.
BEP 2, or Binance Chain Evolution Proposal 2, is a technical standard used for the issuance and implementation of tokens on the Binance chain.
BFA
A Brute Force Attack (BFA), also known as an exhaustive search, is a cryptographic hack that relies on guessing possible combinations of a targeted password until the correct password is discovered.
Burned
Cryptocurrency tokens or coins are considered “burned” when they have been purposely and permanently removed from circulation.
BFT
Byzantine fault tolerance (BFT) is the property of a system that can resist the class of failures derived from the Byzantine Generals’ Problem. This means that a BFT system can continue operating even if some of the nodes fail or act maliciously.
#C
Cryptocurrency / Crypto
A cryptocurrency (crypto) is a digital or virtual currency that uses cryptographic technologies to secure their operation. Most cryptocurrencies are decentralized networks based on blockchain technology and are not issued by the central bank of a country.
Coin
Coins are any cryptocurrency that has a standalone independent blockchain as opposed to tokens which live on another blockchain.
Coinbase
In mineable cryptocurrencies, a coinbase is the number of coins that are generated from scratch and awarded to miners for mining every new block.
Cryptography
In computer science, cryptography refers to is the practice and study of securing information and communication using mathematical concepts and algorithms, to transform messages in ways that are hard to decipher.
Confirmation
In cryptocurrency, a confirmation is a measure of how many blocks have passed since a transaction was added to a blockchain. Each new block is an additional confirmation for that transaction.
Consensus Mechanism
Consensus is achieved when all participants of the network agree on the order and content of the blocks in the blockchain. A consensus mechanism is an underlying technology behind the main functionalities of all blockchain technology, making them an essential operating feature for all cryptocurrencies.
Circulating Supply
The best approximation of the number of coins that are circulating in the market and in the hands of the general public.
A cryptocurrency wallet is in cold storage when it’s not connected to the internet. This includes offline storage of cryptocurrencies, typically involving hardware non-custodial wallets, offline computers, or paper wallets.
Core Wallet
A core wallet contains the entire blockchain as opposed to a piece of it and allows users to not only receive, store and send crypto but also program on or with it.
Centralized Exchange (CEX)
Centralized exchanges (CEXs) are a type of cryptocurrency exchange that is operated by a company which owns and controls it.
Censorship Resistance
Censorship resistance refers to the idea that no party can prevent anyone from participating in a given platform or network.
CeDeFi
CeDeFi, or centralized decentralized finance, combines traditional centralized financial services with decentralized applications, merging conventional regulatory policies with modern financial products and infrastructure.
A Central Bank Digital Currency (CBDC) is the digital form of a country’s fiat currency that is also a claim on the central bank. Instead of printing money, the central bank issues electronic coins or account backed by the full faith and credit of the government.
Chain Split
Chain split, which is another term used to describe a cryptocurrency fork, is the separation of a single original coin into two or more independently managed projects.
Change
Change is a concept relevant to cryptocurrencies that use the UTXO model like Bitcoin. It is the number of coins sent back to a user’s address after they use their unspent outputs to initiate a transaction.
Coin Mixer
Coin mixers allow users to mix up transactions between different cryptocurrency addresses, so they become untraceable and cannot be followed back to the initial sender or receiver of the assets.
Cross-Chain
Cross-chain is a technology that enhances the interconnection between blockchain networks by allowing the exchange of information and value.
Cryptojacking
Cryptojacking is malicious cryptomining that involves infecting third party computers with malwares to use them to mine cryptocurrencies usually without user’s knowledge. Cryptojacking malware can lead to slowdowns and crashes due to straining of computational resources.
Cypherpunk
A cypherpunk is any individual advocating widespread use of strong cryptography and privacy-enhancing technologies as a route to social and political change.
#D
DLT
Distributed Ledger Technology (DLT) is another term for blockchain technology. It is a database that is consensually shared and synchronized across multiple sites, institutions, or geographies, accessible by multiple people.
DApps
Decentralized applications (dApps) are digital applications or programs that exist and run on a blockchain instead of a single server and are outside the purview and control of any controlling authority.
DAO
A Decentralized Autonomous Organization (DAO) is an organization represented by rules encoded as a computer program that is transparent, controlled by the organization members and not influenced by a central authority.
“Digital Currency Electronic Payment” (DCEP) is the national digital currency of China built using Blockchain and Cryptographic technology. DCEP is pegged 1:1 with the Chinese national currency.
Derivatives trading
A derivative is a contract or product that derives its value from an underlying asset. Depending upon the conditions of a contract, derivatives can be categorized as Futures, Forwards, Options and Swaps. By opening a demat account and a trading, you can get started with trading derivatives.
DEX
Decentralized Exchange or DEX is a peer-to-peer exchange allowing users to trade cryptocurrency without the need for an intermediary.
Difficulty
Difficulty is a measure of how difficult it is to mine a block in a blockchain for a particular cryptocurrency. It is a parameter that cryptocurrencies use to keep the average time between blocks steady as the network’s hash power changes.
Dominance
Bitcoin Dominance is a measure of Bitcoin’s value in the context of the larger cryptocurrency market. It can help you understand if altcoins are in a downtrend or uptrend against BTC.
Double Spending
Double Spending is the potential for a cryptocurrency to be spent twice. It occurs when a blockchain network is disrupted and cryptocurrency is essentially stolen.
Dusting Attack
A dusting attack is an attack in which a trace amount of crypto, called dust, is sent to several wallet addresses. This attack is deployed in order to track these addresses with the hope of “un-masking” or de-anonymizing them.
Dump
A sudden drop in the price of an asset.
DYOR
DYOR is an acronym for Do Your Own Research, encouraging investors to complete due diligence into a project before investing.
DeFi or Decentralized Finance is a blanket term for decentralized alternatives to traditional (centralized) finance. It is a blockchain-based form of finance that does not rely on central financial intermediaries, making them open for anyone to use, rather than going through middlemen like banks or brokerages.
DeFi Degens
Degens is shorthand for Degenerate. Degen trading or Degen mode is when a trader invests without proper due diligence and research into a project and speculate on the price swings.
Dead Cat Bounce
A dead cat bounce is a trading jargon meaning a temporary, short-lived recovery of asset prices from a prolonged decline or a bear market that is followed by the continuation of the downtrend.
DPoS
Delegated Proof of Stake (DPoS) is a popular evolution of the PoS concept, whereby users of the network vote and elect delegates to validate the next block.
Dip
A dip is when markets experience a short or protracted downturn in prices.
DDoS attack
DDoS stands for ‘distributed denial of service’. Such attacks attempt to render a site to a halt by overloading it with traffic.
#E
EEA
Enterprise Ethereum Alliance (EEA) is a group of organizations and companies working together to further develop the Ethereum network.
EIP
Ethereum Improvement Proposals (EIPs) describe standards for the Ethereum platform, including core protocol specifications, client APIs, and contract standards.
Ethereum is a decentralized, open source blockchain with smart contract functionality. Ether is the native cryptocurrency of the platform. After Bitcoin, it is the second-largest cryptocurrency by market capitalization and is the most actively used blockchain.
ERC20 is a token standard used for creating and issuing smart contracts on the Ethereum blockchain. ERC stands for “Ethereum Request for Comment,” and it enables smart contracts to operate as tradeable tokens.
ERC-721
ERC 721 is a token standard that describes how to build non-fungible (unique tokens) on the Ethereum blockchain.
ERC-1155 is a digital token standard created by Enjin that can be used to create both fungible (currencies) and non-fungible (digital cards, pets and in-game skins) assets on the Ethereum Network.
EVM
Ethereum Virtual Machine (EVM) is a Turing-complete virtual machine that enables execution of code as intended on the Ethereum network. It is the runtime environment for every smart contract and every Ethereum node runs on the EVM to maintain consensus across the blockchain.
ELI5
ELI5 is short for “Explain Like I’m Five” is a plea for simplicity when crypto concepts are being explained.
Cryptocurrency exchanges are a marketplace where users can trade cryptocurrencies for fiat money or other cryptocurrencies.
Exchange Traded Fund (ETF)
A security that tracks a basket of assets such as stocks, bonds, and cryptocurrencies but can be traded like a single stock.
#F
51% attack
A theoretical attack where if an entity gains 51% of the hashing power, they can perform double-spends and other malicious activities on a cryptocurrency.
Fiat
Fiat money is government-issued currency that is not backed by a physical commodity, such as gold or silver, but rather by the government that issued it. It can take the form of physical cash, or it can be represented electronically, such as with bank credit.
FOMO
An acronym that stands for “Fear of Missing Out” and in the context of investing, refers to the feeling of apprehension for missing out on a potentially profitable investment opportunity and regretting it later.
FUD
An acronym that stands for “Fear, Uncertainty and Doubt.” It is a strategy to influence perception of certain cryptocurrencies or the market as a whole in general by spreading negative, misleading or false information.
Flash Crash
A flash crash is a market condition where an asset’s price falls very rapidly within a very brief time interval.
Flash Loans
Flash loans are a new type of uncollateralized loans enforced by smart contracts. They enable you to borrow instantly without collateral, provided that liquidity is returned to the pool within one transaction.
Flippening
A hypothetical situation whereby the total market cap of Ethereum surpasses the total market cap of Bitcoin.
Full Node
Nodes that download and maintain a blockchain’s entire history in order to observe and enforce its rules.
All cryptocurrency derivatives exchanges use funding rates for perpetual contracts. Funding rates are periodic payments to long or short traders based on the difference between the perpetual contract market and the spot price. Depending on open positions, traders will either pay or receive funding.
Fungible
In cryptocurrency, fungibility is when a coin or token have identical characteristics and can therefore be interchanged easily.
A futures contract is a standardized legal agreement to buy or sell a particular asset at a predetermined quantity, price and at a specified time in the future.
#G
Gas
Gas refers to a unit of measuring the computational effort of conducting transactions or smart contracts on the Ethereum network. It is the price you are willing to pay to miners for a transaction.
Genesis Block
Genesis Block is the first block of data that is processed and validated to form a new blockchain, often referred to as block 0 or block 1.
GitHub
GitHub is one of the most popular code hosting platforms, allowing developers to collaborate on various projects.
Governance
In the world of cryptocurrencies, governance is defined as the people or organizations that have decision-making powers regarding the project.
Governance Token
Governance tokens are tokens that developers create to allow token holders to help shape the future of a protocol. Governance token holders can influence decisions concerning the project such as proposing or deciding on new feature proposals and even changing the governance system itself.
Gwei
Gwei is short for gigawei, or 1,000,000,000 wei. Wei, as the smallest (base) unit of ether, similar to a satoshi in bitcoin. Gwei is used in defining the cost of gas in transactions involving Ether.
Goxxed
Goxxed comes from the infamous MtGox hack and refers to a situation when someone leaves their cryptocurrency in an exchange which gets hacked resulting in the loss of funds for the investor.
#H
HODL
“HODL,” which stands for “Hold On for Dear Life” is a term used by members in the crypto industry to express the will to wait and hold a cryptocurrency for a long period of time, regardless of any changes in the price or markets. The acronym originally came from a misspelling of the world “hold”.
Halving
An event in which the total rewards, in the form of newly generated crypto, awarded to miners to mine blocks is halved.
Hard Cap
A hard cap is the absolute maximum supply of a digital asset.
Hard fork
A hard fork is a radical update to the blockchain that creates a permanent change to a digital currency’s protocol. They result in a whole new blockchain, which does not accept any blocks mined using the old rules, leading to a scenario where both the old and the new blockchains exist simultaneously.
A hardware wallet is a physical wallet for cryptocurrencies that usually resemble a USB stick. They are one of the safest ways to store your cryptocurrencies since they are not connected to the internet.
Hot storage refers to any crypto wallet that is run through an internet connected system. Hot wallets can be run on the cloud, a mobile device, or a desktop allowing for quicker access to the cryptocurrency.
Hierarchical Deterministic Wallet (HD Wallet)
A Hierarchical Deterministic (HD) Wallet generates a new key pair from a master key pair for each crypto transaction to enhance privacy and security. Its hierarchical structure resembles that of a tree, with the master key “determining” the key pairs that follow it in the hierarchy.
Hash Function
A hash function is a mathematical function that converts an input of an arbitrary length into an encrypted output of a fixed length. This means regardless of the original amount of data or file size involved, its unique hash will always be the same size. Bitcoin uses the SHA256 hashing algorithm.
Hash Rate
Hash Rate refers to the total combined computational power that is being used to mine and process transactions on a Proof-of-Work blockchain.
Honeyminer
Honeyminer is a cryptocurrency mining app available for download on multiple devices. It allows users to participate in a dynamic mining pool by running the app when the computer’s GPU isn’t in use.
#I
ICO
Comparable to the traditional Initial Public Offering (IPO), an Initial Coin Offering (ICO) is a type of crowdfunding using cryptocurrency tokens as a means of raising capital for early-stage companies.
IDO
An initial DEX offering or IDO refers to the launching of a cryptocurrency on a decentralized exchange (DEX) in order to raise funding from retail investors.
IEO
Initial exchange offering (IEO) is a variant of initial coin offerings, operated directly by cryptocurrency exchanges. It is a type of crowdfunding where crypto start-ups generate capital by listing through a centralized crypto exchange.
IBO
An Initial Bounty Offering or IBO is a novel way of launching a project with tokens distributed to individuals who contribute time and skills to a platform, rather than their money.
Impermanent Loss
Impermanent loss describes the temporary loss of funds experienced by liquidity providers because of volatility in a trading pair. It occurs when you provide liquidity to a liquidity pool, and the price of your deposited assets changes compared to when you deposited them.
Infinite Approval
Infinite approval is a smart contract programming practice, giving a smart contract authorization to access unlimited number of tokens from the user’s wallet.
INO
An Initial NFT Offering (INO) refers to an initial offering of a limited set of NFTs for sale on a particular NFT marketplace. Projects do this as a form of crowdfunding.
Instamine
An instamine occurs when a large quantity of cryptocurrency tokens are brought into existence at once.
#K
KYC
Short for Know Your Customer, KYC is a compliance term referred to checks that crypto exchanges and trading platforms must complete to verify the identity of their customers. They are imposed by regulators who require identity background checks to deter money laundering and terrorist funding.
#L
Long
Going long or having a long position, means making a wager that an asset will rise in value. If a trader purchases a digital currency like bitcoin, they are making a bet that the cryptocurrency will appreciate.
Limit Order
A limit order is a type of exchange order that allows traders to purchase or sell a cryptocurrency at a specified price or better. It allows you to set your own price to buy or sell. If the market reaches your limit price, your order will be executed.
Leverage
Money that a trader can borrow from a brokerage, enabling them to gain a greater exposure to a position than what their capital allows.
Liquidation
The term liquidation simply means selling assets for fiat. Forced liquidation happens when the trader is unable to fulfill margin requirements for a leveraged position when the market goes against their trade.
Liquidity
liquidity refers to how easily a cryptocurrency can be bought and sold without greatly impacting the overall market price.
Liquidity Pool
Liquidity pools are pools of tokens locked in smart contracts that provide liquidity in decentralized exchanges to reduce the problems caused by the illiquidity typical of such systems.
Liquidity Provider
Liquidity providers are decentralized exchange users who fund a liquidity pool with tokens they own.
LP Tokens
Liquidity Provider tokens (LP tokens) are crypto tokens issued to liquidity providers on a decentralized exchange in return for providing liquidity. LP tokens represent a liquidity provider’s share of a pool.
Layer 2
Layer 2 refers to a secondary framework or protocol that is built on top of an existing blockchain system. The goal is to solve the transaction speed and scaling difficulties being faced by cryptocurrency networks in their base layer.
A second-layer protocol that is designed to solve Bitcoin’s scalability problem by allowing transactions to be processed more quickly.
Facebook unveiled the Libra project in 2019 with a vision of being a stablecoin backed by multiple fiat currencies. Due to international regulatory backlash, on April 2020 Libra rebranded to Diem with the team indicating it would launch an array of stablecoins, each backed by a single fiat currency.
#M
Moon
A term often employed as a verb (mooning) to describe a cryptocurrency that is under a strong upward market trend. The phrase “to the moon,” refers to a belief that a cryptocurrency is going to rise significantly in price.
Market Cap
Market cap is short for market capitalization, which is the total market value of a cryptocurrency. It is calculated by multiplying the number coins outstanding by the price per coin.
Max Supply
The best approximation of the maximum amount of coins that will ever exist in the lifetime of the cryptocurrency.
Mempool
A mempool is the digital database maintained by miners, where all unconfirmed transactions generated on the blockchain network are parked before they are sequentially aggregated into blocks.
Merkle Tree
A Merkle tree, is a mathematical data structure composed of hashes of different blocks of data, and which serves as a summary of all the transactions in a block. It also allows for efficient and secure verification and helps to verify the consistency and content of the data in blockchain.
A mnemonic phrase (also known as mnemonic seed, or seed phrase) is a cryptographically derived security code composed of a list of random words in a specific order, typically ranging between 12 and 14, which is used to recover a cryptocurrency wallet.
Multi-Sig Wallet
Multi Signature (Multi-Sig) wallets, are cryptocurrency wallets that require two or more private keys to sign and send a transaction.
Mineable
Cryptocurrencies are said to be mineable when they have a system through which miners are rewarded with newly created coins for verifying unconfirmed transactions through contributing hash power.
Mining is the process of verifying new transactions on a blockchain by miners. This verification requires hardware and electricity, and miners are rewarded with newly minted crypto for performing this task.
Miners
Miners are individuals with computers and processors across the globe who verify transactions, bundle them in a block and add their block to the existing blockchain. They also maintain a copy of all the transaction ever made on a blockchain network.
Mining Pool
A setup where multiple miners combine their computing power to gain economies of scale and competitiveness in finding the next block on a blockchain, with rewards split among participants.
Market Maker, Market Taker
A Market maker places an order (to buy or sell at a quoted price), while a Market taker accepts that placed order (to execute the buy or sell at the quoted price).
Market Order
A market order is an instant buy or sell of a cryptocurrency for the best available price at that time, in contrast to limit orders where a cryptocurrency is bought or sold only at a specified price.
Margin Trading
A practice where a trader uses borrowed funds from a broker to trade a cryptocurrency, which forms the collateral for the loan from the broker. It can be relatively risky for inexperienced traders who may receive a margin call if the market moves in the opposite direction of their trades.
Margin Call
A margin call occurs when the value of an investor’s margin account falls below the broker’s required amount. When a margin call occurs, the investor must choose to either deposit more money in the account or sell some of the assets held in their account.
Metaverse
A virtual world which is created mostly for people to connect socially, play games, and interact using their digital avatars. They can also further enhance their experience in the metaverse with the use of virtual or augmented reality headsets. The recent popularity of metaverses have also resulted in many companies taking advantage of this trend by hosting concerts, NFT launches, and digital fashion experiences.
#N
Noob
Newcomers are frequently described as “noobs” by industry insiders.
Node
A node is the most basic unit of a blockchain infrastructure. It is a computer connected to other computers which follows protocol rules, shares information and stores data. A full node is a computer which hosts and synchronizes a copy of the entire blockchain for a cryptocurrency.
Non-Fungible Tokens (NFTs) are unique cryptographic tokens that we can use to represent ownership of unique items. It is non-replicable, can’t be substituted, and can only have one official owner at a time.
NGMI
An abbreviation of “Not Gonna Make It”, it is the opposite of WAGMI (We Are Gonna Make It) and is often used when commenting on bad decisions by cryptocurrency traders or blockchain projects.
Nonce
Number only used once (Nonce) which, in the context of cryptocurrency mining, is a number which, when added to a hashed block, meets the difficulty level restrictions. When competing to mine a new block, the first miner to find the nonce is granted the right to add the next block into the blockchain.
#O
On-Chain
Transactions that are recorded on the blockchain itself and can be viewed publicly.
Open Source
Open source is a philosophy, with participants believing in the free and open sharing of information in pursuit of the greater common good. In software development, the source code of an open source software is made available to developers and users to modify as they see fit.
Orphaned Block / Stale Block
An orphan block is a valid block that has been solved within the blockchain network but was not accepted to the main chain due to a lag within the network itself.
Oracles
Blockchain oracles are third-party services that provide smart contracts with external information. They serve as bridges between blockchains and the outside world.
Order Book
Order book is the list of all open orders that are currently available on an exchange for a specific trading pair, organized by price level.
OTC
Over the Counter (OTC) is defined as a transaction made outside of an exchange, often peer-to-peer through private trades.
#P
PAX Gold (PAXG)
PAX Gold is the first gold-backed and fully regulated digital asset. It represents physical gold bars, with its value tied directly to the real-time market value of the physical gold it represents.
A private key, made up of a series of alphanumeric characters, is the password that an investor needs to access their digital currency. While anyone can send transactions to the public key, you need the private key to “unlock” them and prove that you are the owner of the cryptocurrency received in the transaction.
A public key, made up of a series of alphanumeric characters, is the address that you share with people so you can receive cryptocurrency.
Public Address
A public address is the cryptographic hash of a public key, allowing the user to use it as an address to request for payment.
Proof-of-Work (PoW) is a blockchain consensus mechanism involving solving of computationally intensive puzzles by miners to validate transactions and create new blocks in return for rewards in the form of newly minted coins.
Proof-of-Stake (PoS) is a blockchain consensus mechanism which allows a miner to validate transactions without spending much electricity, based on the number of coins they have staked in the network. The idea is that a miner will risk losing their stake if they act in a malicious manner.
PoA
Proof-of-Authority (PoA) is a blockchain consensus mechanism that uses identity as a stake. A few specific nodes are granted the authority to approve a miner’s ability to create a block. This is a faster alternative to the proof-of-work model, but more centralized.
DPoS
Delegated Proof of Stake (DPoS) is a consensus algorithm which is an advancement of the fundamental concepts of PoS. Stakeholders vote for a few delegates that secure the network on their behalf who are then responsible for achieving consensus. The voting power is proportional to the number of coins each user holds.
Privacy coin
A cryptocurrency that is completely anonymous and private as individual transactions cannot be tracked on the blockchain. Some of the most well-known privacy coins include Monero, Dash, and Zcash.
P2P
Peer-to-Peer (P2P) is the decentralized interactions between parties involving sharing transactions, files or other resources with no middleman in between.
Paper Wallet
A paper wallet is a form of cold storage where the private key or seed phrase is written or printed on a piece of paper which the user can then store.
Pump and Dump
A “pump and dump” is a type of securities fraud where a market participant, or several participants working together to falsely inflate the price of an asset in order to sell already established position when prices are artificially inflated.
#R
REKT
REKT is a shorthand for the word “wrecked” describing a significant loss in a trade.
ROI
Return on investment (ROI) is a performance measure used to evaluate the profitability of an investment. It is calculated by dividing the profit (return) made on an investment by the initial cost of the investment.
Replay Attack
A replay attack, sometimes also called a playback attack, is a cyber-attack in which the malicious entity intercepts and then repeats a valid data transmission going through a network.
Rug Pull
A rug pull is a type of exit scam whereby malicious developers abandon a project and escape with investor funds by removing liquidity from a coin pair in a Decentralized Exchange thereby crashing its price.
#S
Satoshi Nakamoto
Satoshi Nakamoto is the individual, or group of individuals, credited with founding the world’s first cryptocurrency, Bitcoin. The identity of Satoshi Nakamoto has not yet been confirmed.
Satoshi
A Satoshi is the smallest denomination of Bitcoin and is equivalent to 100th billionth of one Bitcoin (0.00000001 BTC). It was named after Bitcoin’s creator, Satoshi Nakamoto.
Stablecoin
Stablecoin as the name suggests is a cryptocurrency that is tied to the value of something with extremely low volatility, such as the US dollar, to make it more stable and less volatile in price swings.
SHA-256
Secure Hashing Algorithm (SHA) -256 is the hash function and mining algorithm of the Bitcoin protocol. It moderates the creation and management of addresses and is also used for transaction verification.
Smart Contract
Smart contracts are small pieces of code that runs on a Turing complete blockchain like Ethereum. They are typically used to automate the execution of an agreement so that all participants can be certain of the outcome, without the involvement of any intermediary.
A smart contract audit is an extensive methodical examination and analysis of a smart contract’s code by a leading security auditing company. This process is conducted to discover errors, issues and security vulnerabilities in the code in order to suggest improvements and ways to fix them.
Soft Fork
A soft fork is a backward-compatible protocol upgrade, meaning the upgraded nodes can communicate with the non-upgraded ones. The addition of a new rule that doesn’t clash with the older rules.
Segregated Witness (SegWit) is a Bitcoin Improvement Proposal (BIP) aimed to fix transaction malleability on Bitcoin. It refers to a soft fork that separated digital signature data from transaction data, allowing more transactions to fit on one block.
Staking
Staking is an activity where a user locks or holds his funds in a cryptocurrency wallet to participate in maintaining the operations of a proof-of-stake (PoS)-based blockchain system.
Sharding
Sharding is a scaling approach by splitting a blockchain network into separate shards (smaller pieces), each with its own data, separate from other shards, so as to support more users and increase transaction throughput than the base layer.
Solidity
Solidity is the programming language developed and used by Ethereum developers for writing smart contracts.
Side Chain
A blockchain ledger that runs in parallel to a primary blockchain, where there is a two-way link between the primary chain and sidechain.
Security Token
A security token is essentially a digital form of traditional securities and will therefore be subjected to securities registration requirement.
STO
A security token offering (STO) is a public offering where tokenized digital securities are sold to public.
Slippage
Slippage happens when traders must settle for a different price than what they initially requested due to a movement in price between the time the order enters the market and the execution of a trade.
Short/Shorting
Shorting an asset, also known as taking a short position, means making a bet that the asset will fall in value. It is the act of selling the cryptocurrency in the hope that it falls in value and you can buy it back at a lower price thereby profiting from the difference in market price.
Shilling
The act of enthusiastically promoting a cryptocurrency or blockchain project.
Shitcoin
A coin with no obvious potential value or usage.
#T
Technical Analysis (TA) attempts to understand the market sentiment behind price trends by looking for patterns and trends rather than analyzing an asset’s fundamental attributes. It is used to scrutinize the ways supply and demand for an asset affect changes in price, volume and volatility.
Turing-Complete
Turing Complete refers to a machine that, given enough time and memory along with the necessary instructions, can solve any computational problem, no matter how complex.
Token
Tokens are cryptocurrencies that do not have their own blockchain but live on another blockchain like Ethereum, as opposed to Coins which are any cryptocurrency that has a standalone independent blockchain.
TPS
Transactions per second (TPS) refers to the number of transactions that a network is capable of processing each second.
TVL
Total Value Locked (TVL) represents the number of assets that are currently being staked in a specific protocol.
2FA
Two-factor authentication (2FA), sometimes referred to as two-step verification or dual-factor authentication, is a security process in which users provide two different authentication factors to verify themselves to better protect both the user’s credentials and the resources the user can access.
Testnet
A testnet is an alternative blockchain used by developers for testing and experimentation without risk to real funds or the main chain.
Timestamp
A form of identification for when a certain transaction occurred, usually with date and time of day and accurate to fractions of a second.
Taproot
Taproot is an instantiation of a soft fork for Bitcoin, intended to both improve privacy and improve other aspects tied to more complex transactions.
TLT
Think Long Term (TLT) is a mindset where you have a longer-term investment horizon.
#U
UTXO
An unspent transaction output (UTXO) refers to a transaction output that can be used as input in a new transaction. These are the transactions that are left unspent after completing a transaction, similar to the change someone receives after conducting a cash transaction at a store.
Utility Token
A cryptocurrency that can be used for purposes aside from transactions. When a project creates a utility token, it is essentially creating a form of a digital coupon that can be redeemed in the future for discounted fees or special access to a product or service.
#V
Vanity Address
A cryptocurrency public address with custom letters and numbers, usually picked by its owner.
Virgin Bitcoin
A bitcoin that has never been spent.
Validator
A blockchain validator is someone who is responsible for verifying transactions on a blockchain.
#W
Whale
A term used to describe investors who have uncommonly large amounts of crypto, especially those with enough funds to manipulate the market.
WAGMI
Short for “We All Gonna Make It”, this term is used amongst cryptocurrency traders to reassure each other when the market or a specific cryptocurrency is not performing well.
Wallet
A crypto wallet is the place where cryptocurrencies are stored and from where a user can send and receive digital assets. Wallets come in a variety of forms, including hardware and software.
Whitepaper
A white paper is a document released by a project that outlines what a cryptocurrency is created to do by providing technical information about its concept, and a roadmap for how it plans to grow and succeed.
Whitelist
The term whitelist refers to a list of allowed and identified individuals, institutions, computer programs, or even cryptocurrency addresses in an initial offering of tokens by a project.
Weak Hands
An investor prone to panic selling at the first sign of a price decline.
When Lambo
When Lambo is a slang referring to cryptocurrency holders hoping to become rich enough to afford the purchase of a Lamborghini, or any such expensive car, with the profits.
When Moon
A phrase used to ask when the price of cryptocurrencies will rise exponentially.
The Wyckoff Pattern, developed by Richard Wyckoff, an early 20th-century, is a chart pattern which centered around the realization that price trends were driven primarily by institutional and other large operators who manipulate markets in their favor.
#Y
Yield farming involves earning interest by investing crypto in decentralized finance markets.
#Z
Zero-Knowledge Proof
Zero-knowledge Proof is an encryption scheme in which one party (the Prover) can prove that a specific statement is true to the other party (the Verifier) without disclosing any additional information.
Disclaimer: Cryptocurrency trading involves significant risks and may result in the loss of your capital. You should carefully consider whether trading cryptocurrencies is right for you in light of your financial condition and ability to bear financial risks. Cryptocurrency prices are highly volatile and can fluctuate widely in a short period of time. As such, trading cryptocurrencies may not be suitable for everyone. Additionally, storing cryptocurrencies on a centralized exchange carries inherent risks, including the potential for loss due to hacking, exchange collapse, or other security breaches. We strongly advise that you seek independent professional advice before engaging in any cryptocurrency trading activities and carefully consider the security measures in place when choosing or storing your cryptocurrencies on a cryptocurrency exchange.


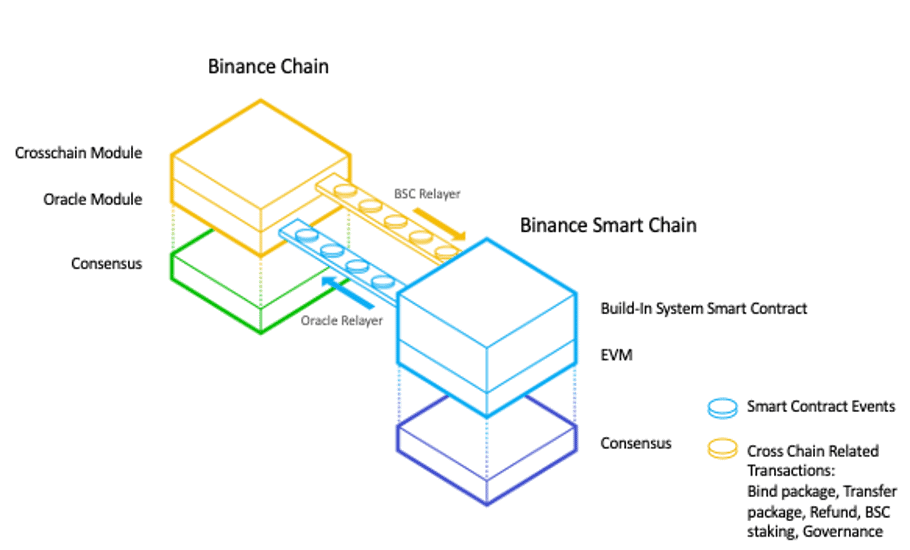
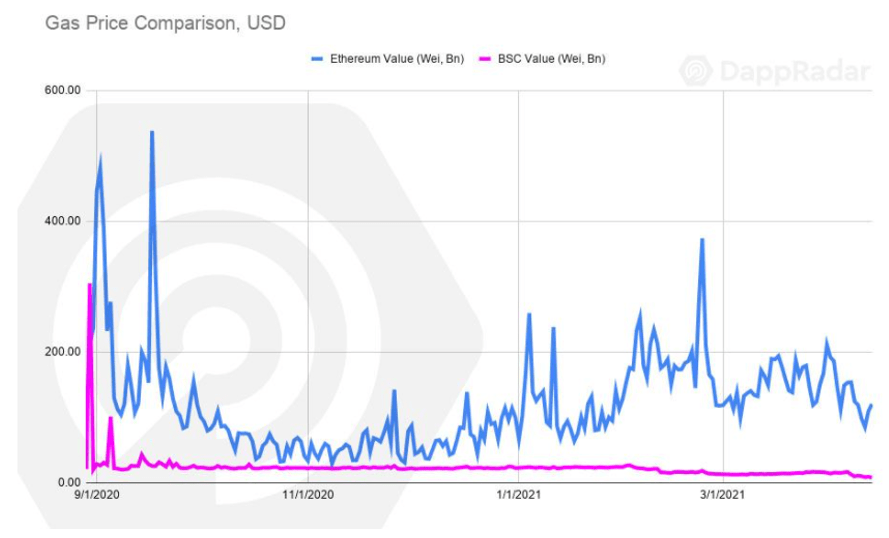
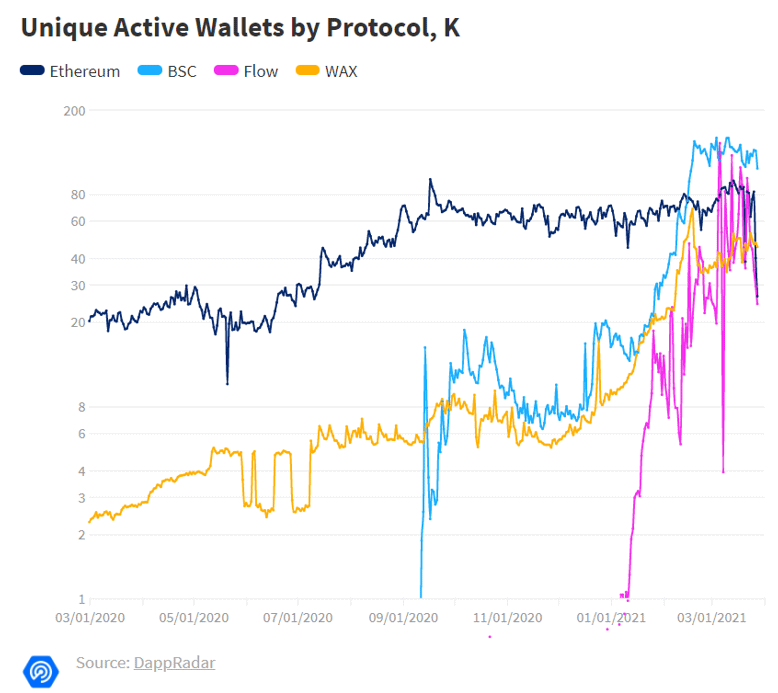






 Key Features of Binance
Key Features of Binance